Unlocking the Fortress: An Introduction to Two-Factor Authentication
In today’s digital realm, our devices and online accounts have become integral to our daily lives, but with this convenience comes the ever-lurking threat of cyberattacks. As malicious actors grow ever-more sophisticated, traditional passwords alone prove insufficient to safeguard our digital realm. Cue two-factor authentication (2FA), a vital layer of security that strengthens the defense surrounding our valuable data.

Image: www.exeideas.com
2FA operates on a simple yet ingenious principle: requiring two different forms of authentication when accessing an account. Typically, this involves a primary method (such as a password or PIN) and a secondary method, like a one-time password (OTP) or a physical security key. This multi-layered approach ensures that even if an attacker obtains your password, they’ll be unable to access your account without the second factor.**
Empowering Users: The Role of Two-Factor Authentication in Cybersecurity
The benefits of 2FA are undeniable. By introducing an additional barrier, it significantly reduces the risk of unauthorized account access. As malicious actors often target weak or stolen passwords, 2FA thwarts their efforts by requiring an additional layer of validation.
Furthermore, 2FA can empower users to take an active role in safeguarding their accounts. By choosing a method that meets their specific needs and preferences, individuals can create a personalized security solution that balances convenience with robust protection.
Unveiling the Layers: Different Types of Two-Factor Authentication Methods
To accommodate the diverse needs of users, 2FA offers a range of authentication methods. One of the most common is OTP-based authentication, where a unique, time-sensitive code is sent to the user’s linked device via SMS or email. This code must be entered in addition to the primary password.
For enhanced security, hardware-based authentication is a preferred choice. Utilizing a physical device like a USB key or a mobile app, this method generates OTPs without the need for network connectivity or SMS verification.
Transcending Boundaries: Applications of Two-Factor Authentication
The versatility of 2FA extends across a wide spectrum of devices and platforms. From accessing online banking accounts to unlocking social media profiles, its applications are far-reaching. Moreover, major platforms such as Google, Amazon, and Microsoft have incorporated 2FA into their ecosystem, making it a ubiquitous safeguard for modern users.
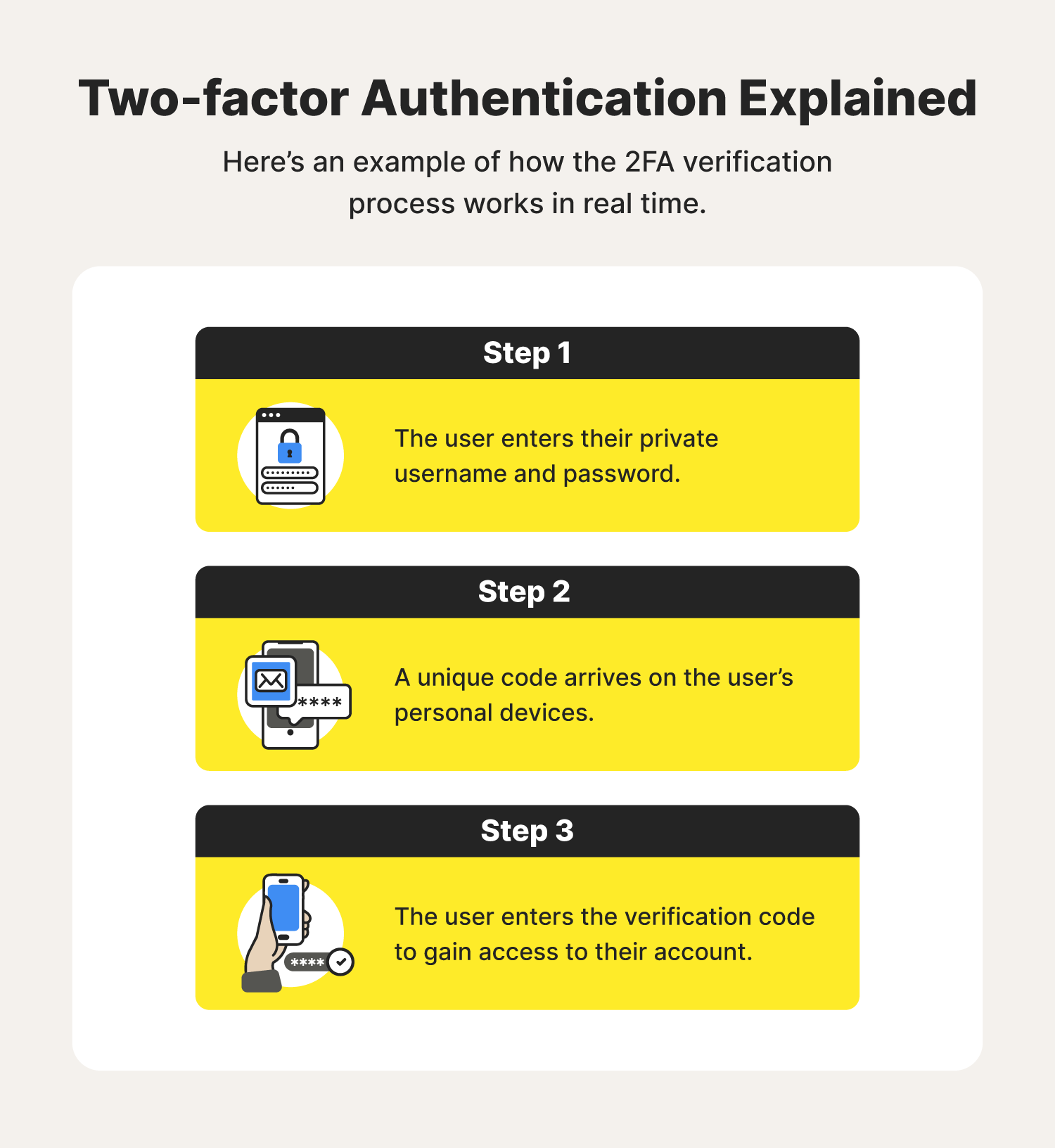
Image: us.norton.com
Expert’s Insights: Amplifying the Benefits of Two-Factor Authentication
Renowned cybersecurity expert Dr. Alexander Vega emphasizes, “Two-factor authentication is a crucial step toward enhancing your digital security. By implementing it, you’re essentially adding a second lock to your digital door, making it significantly harder for unauthorized individuals to gain access to your accounts.”
Additionally, Professor Emily Carter highlights the user-centric nature of 2FA, stating, “By choosing a method that aligns with your personal preferences and security concerns, you’re creating a tailored defense system that empowers you in the fight against cybercrime.”
Importance Of Two Factor Authentication
Unlocking a Safer Digital Future: The Call to Embrace Two-Factor Authentication
In the ever-evolving landscape of cybersecurity, two-factor authentication emerges as a beacon of protection, deterring malicious actors and ensuring the safety of our digital lives. Let us embrace this invaluable safeguard and unlock the path toward a more secure and empowered digital realm.







